Is your pilot flying without a license?

Fake Digital Credentials: The Problem and a Solution
In the ongoing era of digital transformation, an ever-increasing number of interactions and functionalities are migrating into the online and digital realm. One implication for the educational sector is that digital rather than physical credentials will become the new norm.
There are many advantages associated with credentials being issued in digital form but also substantial problems. In particular, digital credentials are trivial to falsify and very hard to verify. To quantify the problem, the global revenue generated through the sale of fake credentials in 2022 is estimated to be more than $21 billion. The following describes the implications of widespread fake credentials and how this problem can be solved.
The problem of fake credentials
Fake credentials create severe issues for three stakeholders: employers, holders of valid credentials, and credential issuers.
Employers are harmed because they choose between going through a costly and imperfect verification process and the risk of hiring a candidate with fake credentials. The former is expensive, and the latter may result in unqualified hires with a demonstrated willingness to engage in fraud.
Holders of valid credentials are harmed because the difficulty of verifying their credentials results in a discount on their hard-earned achievements and because employers may mistakenly hire holders of fake credentials.
Credential issuers suffer because the lower credibility of valid credentials reduces their students’ willingness to pay for education. Moreover, fraudsters claiming to be graduates damage the issuer’s reputation, diluting the institution’s brand.
Finally, there is potential overarching damage to society. Two extreme examples are pilots and medical doctors with fake credentials. These are not purely hypothetical risks.
- An investigation of Pakistani aviation authorities that concluded in 2020 found that 260 of 860 active Pakistani pilots did not have a valid license.
- The Indian Medical Association estimates that 700,000 practicing doctors and nurses in India have no formal training nor degree. The concerns associated with this fact reach far beyond India’s borders. India is the world’s largest “exporter” of medical doctors, with the US being the number one destination country.
- 30% of job seekers in large US surveys admit to lying on their resume.
Standard Measures to Prevent Credential Fraud
There are two standard approaches to credential verification. The first is call-backs, where an employer calls the university to verify a candidate’s credential. This requires time and human resources for both the employer and the university and is thus costly.
The second approach is to (partially) automate the verification process through an intermediary. While this approach is likely more cost-efficient and effectively prevents credential fraud, it gives rise to several concerns for the credential issuers and holders, mainly that all credential information is shared with the intermediary and that this verification approach is only functional as long as the intermediary is willing and able to offer it. Switching to new intermediaries may also be costly or difficult, creating vendor lock-in for issuers.
A Cryptography and Blockchain-Based Solution to Fake Credentials
An optimal solution preventing fake credentials would thus have several characteristics:
- It should make it easy to differentiate between valid and counterfeit credentials
- It should retain the privacy of the credential content relative to the service provider
- It should not be subject to a single point of failure where the service provider is required to actively participate in the verification process
At vBase, we have developed a solution that satisfies the above and has additional attractive characteristics. Our solution relies on three innovative technologies. Each digital credential has a unique numerical identifier, formally a hash, which we informally denote as a digital fingerprint. Any infinitesimal change of a digital file results in a change of the fingerprint, the same file always generates the same fingerprint, and the fingerprint reveals nothing about the underlying credential.
The first step of our solution involves computing the fingerprint of the credential. The second step establishes a verifiable link between the credential and its issuer. To do so, we rely on digital signatures, a well-established and robust method to establish the authenticity of digital files. Finally, as a last step we are committing the digital fingerprint and its corresponding digital signature to a blockchain, i.e., a public distributed ledger. This public commitment to a distributed ledger assures the credential’s authenticity is eternally verifiable.
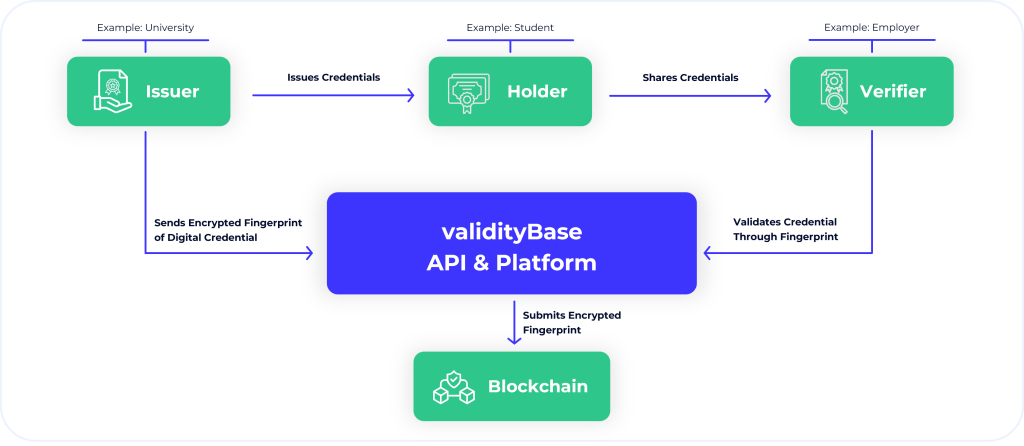
The Process of Verification
While the details of our solution might sound complicated, the practice of it is simple and fast. Consider a university that uses our solution. The university creates a PDF credential for each graduate, computes the fingerprint and signature, and places this information on a blockchain. Thereafter, the university issues the credentials to its graduates.
When applying for a job, the graduate shares the credential with the potential employer. The difference now is that the potential employer can use our verification procedure to compute the digital fingerprint of the credential and check the public blockchain if and by whom it has been signed and committed. As digital signatures are impossible to forge, our solution is robust to forgery, prevents any credential content from leaking to anybody who does not have a copy of the credential, and is not subject to a single point of failure.
Finally, since a credential’s digital signature and fingerprint are stored in a distributed ledger with 1,000s of globally available and officially maintained copies, it is very likely that the proof of authenticity of the credential will far outlive its holder.
Want to learn more?
Contact hello@vbase.com for more information
Recent Posts
 Why Great Returns Don’t Attract Investors
Why Great Returns Don’t Attract Investors
Many investors are unable to convert strong returns into clients or capital. Learn why and how to fix it.
 Mitigating BorgBackup Client Compromise
Mitigating BorgBackup Client Compromise
A compromised BorgBackup client allows undetectable tampering with past backups. vBase offers a simple solution.
 Stop Using Brokerage Statements to Show Your Track Record
Stop Using Brokerage Statements to Show Your Track Record
Many traders use brokerage statements to create a verifiable track record. Unfortunately they are not credible for this purpose. A better alternative exists.